In light of pressing issues such as Prism and others, it is more than advisable to encrypt email communication. An encryption solution of this kind can be implemented in two ways: Using PGP or S/MIME. While PGP uses generated keys, S/MIME employs a certificate. In previous iQ.Suite versions, neither the view, nor the management of the individual S/MIME certificates in the so-called certs.db were sufficient.
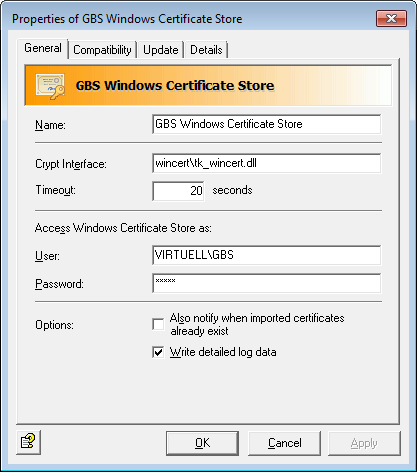
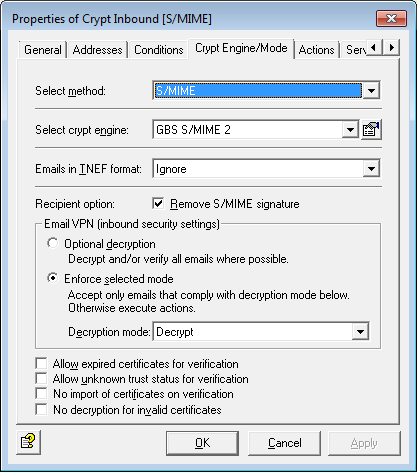
In the latest Version 13 of iQ.Suite for Microsoft Exchange/SMTP, a commonly known management area of the Microsoft world for S/MIME certificates is employed: Windows Certificate Store. It is now possible to view certificates via a user interface, and to manage them based on their status (trustworthy/not trustworthy/unknown).
Step by Step
In order to use Windows Certificate Store for the management of S/MIME certificates, a user with local administrator rights must added to the Microsoft Active Directory. In addition, this administrator must be granted permission to execute batch jobs, which makes it possible to log on to this account:
Local Policies > User Rights Assignment > Log on as Batch Job
Afterwards, the user is added to the settings for the Windows Certificate Store in the iQ.Suite Management Console.
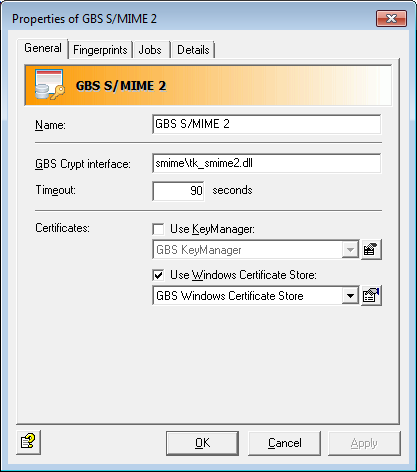
The “Compatibility“ tab is only relevant in the context of migrating iQ.Suite S/MIME to S/MIME 2 Engine. The “Update“ tab is only necessary in relation to GBS’ iQ.Suite KeyManager.
If you have been using the certificate database certs.db, and you wish to continue using certificates it contains, you may now export them.
In an IT infrastructure with multiple iQ.Suite servers, iQ.Suite KeyManager should be considered for the management of S/MIME cerificates. This is configured as a local cache in combination with Windows Certificate Store.